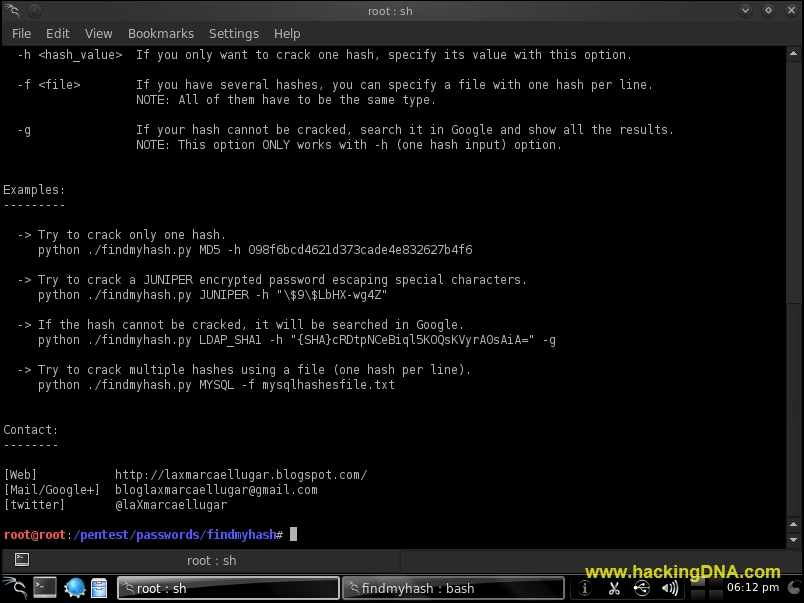
This is a Juniper equivalent to the Cisco Type 7 tool. It will only work with $9$ passwords it will not work with $1$ md5 hash passwords!
It will either take an encrypted password (did i mention its only $9$ types?) and 'crack' it to display the plain text or will encrypt plain text into a usable type $9$ password that can be used on a Juniper device.
An example of a type $9$ is: $9$DMk5Ftu1rK80OvLXxdVHq.fz6B1heK80ORSeW-dUjH
Please note to include the $9$ part of the password.
- This output (invalid password) tells us the PDF document is encrypted with a user password. I’ve written some blog posts about decrypting PDFs, but because we need to perform a brute-force attack here (it’s a short random password), this time I’m going to use hashcat to crack the password. First we need to extract the hash to crack from.
- These passwords are generated after the setupassist.sh script successfully executes during installation. See Generating and Encrypting Passwords for Infrastructure Components. This article explains how to retrieve these dynamic passwords at a later point in time.
- If wpa-psk ascii 0 is used then the ascii text that follows is clear text and its not encrypted. Encryption Methods That Cannot be Decrypted. As opposed to Type 7 Passwords which can easily be decrypted, Secret 5 passwords cannot be decrypted as the password has ben hashed with MD5.
Just pick either encrypt or decrypt and enter your sting.
12:36 pm For those that want to do password encryption using Java instead of Perl below find the Java code to encrypt both $1 and $9 passwords. Clear-cut tool which enables you to retrieve lost or forgotten passwords from your Juniper router with just a click of the button What's new in Juniper Password Decryptor 3.0: Encrypted Password.
Encrypted Password Cracker

Juniper Encrypted Password Crack 1.8
Android emulator for macos catalina. Any problems or suggestions please let me know.
m00nie :D
Bluestacks android emulator for mac os. Have you ever wondered how Junos stores your passwords in configuration? And is there a difference between this one:
and this one:
Bluestacks download mac big sur. Actually, the difference is significant: $1 passwords are “salted” SHA-1 hashes (“salted” means – the calculated hash is different every time, even if the password is the same), and the $9 passwords are just scrambled ones and can be easily reverted to the original plain-text form.
There is an online tool for that, or if you prefer a locally working script, there are some on the Internet, such as this one (Python 2 and 3):
In conclusion, although user’s passwords ($1 ones) can’t be easily recovered from a leaked config, your protocol authentication, FTP password, RADIUS secret, IKE pre-shared key, and some other sensitive keys can be derived from it. So make sure to keep your config backups in a secure place.